Key Insights on Aerospace Cybersecurity
- Rising Vulnerabilities: The aerospace sector faces a 600% surge in cyberattacks year-over-year, driven by interconnected aircraft systems and critical infrastructure, making it a prime target for ransomware, DDoS, and state-sponsored espionage.
- Major Impacts: Incidents like the 2025 Qantas data breach affecting 5.7 million customers and ransomware hits on airports highlight risks to operations, passenger data, and flight safety, with global losses exceeding $1 billion annually.
- Protective Measures: Organizations must adopt layered defenses, including employee training, zero-trust architectures, and AI-driven threat detection, while complying with evolving regulations from bodies like the Federal Aviation Administration (FAA) and International Civil Aviation Organization (ICAO).
- Future Outlook: By 2032, the aerospace cybersecurity market could reach $59.58 billion, fueled by innovations in quantum-safe encryption and autonomous system security, though legacy equipment remains a persistent challenge.
Understanding the Risks
Aerospace cybersecurity involves safeguarding aircraft, satellites, airports, and supply chains from digital intrusions that could disrupt flights or compromise safety. Research suggests that while no major in-flight hacks have occurred, the evidence leans toward increased vulnerabilities as aircraft become more connected, potentially leading to delayed responses or data leaks if unaddressed.
Essential Strategies
To mitigate threats, prioritize risk assessments and regular audits. For instance, implementing firewalls and behavioral analytics can reduce breach risks by up to 70%, according to industry analyses, ensuring smoother operations amid growing digital reliance.
Why It Matters Now
With geopolitical tensions amplifying state actor threats from nations like China and Russia, proactive defenses not only protect assets but also build passenger trust. It seems likely that integrated AI tools will become standard, helping detect anomalies in real-time without overwhelming existing systems.
Table of Contents
In an era where airplanes communicate constantly with ground stations, satellites relay critical data across orbits, and airports manage millions of passengers through digital networks, the skies have never been more vulnerable to invisible enemies. Aerospace cybersecurity isn’t just a technical buzzword—it’s the invisible shield that keeps our global transportation network humming safely. Imagine a world where a single hacked signal could ground a fleet or expose passenger details to the dark web. That’s the reality we’re navigating today, as cyber threats evolve faster than the jet streams.
This article dives deep into the challenges, drawing from expert analyses and real incidents to explore how the industry is fighting back. We’ll uncover the threats lurking in the clouds, the vulnerabilities in our high-flying machines, proven protection strategies, and a glimpse into tomorrow’s defenses. Buckle up; this is a comprehensive flight plan for understanding and securing the digital airways.
The Evolving Threat Landscape in Aerospace
The aerospace world, encompassing commercial aviation, defense systems, and space exploration, has transformed into a digital powerhouse. Modern aircraft aren’t just metal birds—they’re flying computers with embedded sensors, wireless connections, and software that rivals a smartphone’s complexity. This connectivity, while revolutionary, opens doors to cyber mischief. According to recent assessments, cyberattacks on the sector jumped by 600% from 2024 to 2025, with ransomware groups alone launching 27 major assaults. These aren’t random pranks; they’re calculated strikes aimed at disrupting operations, stealing intellectual property, or even influencing geopolitical plays.
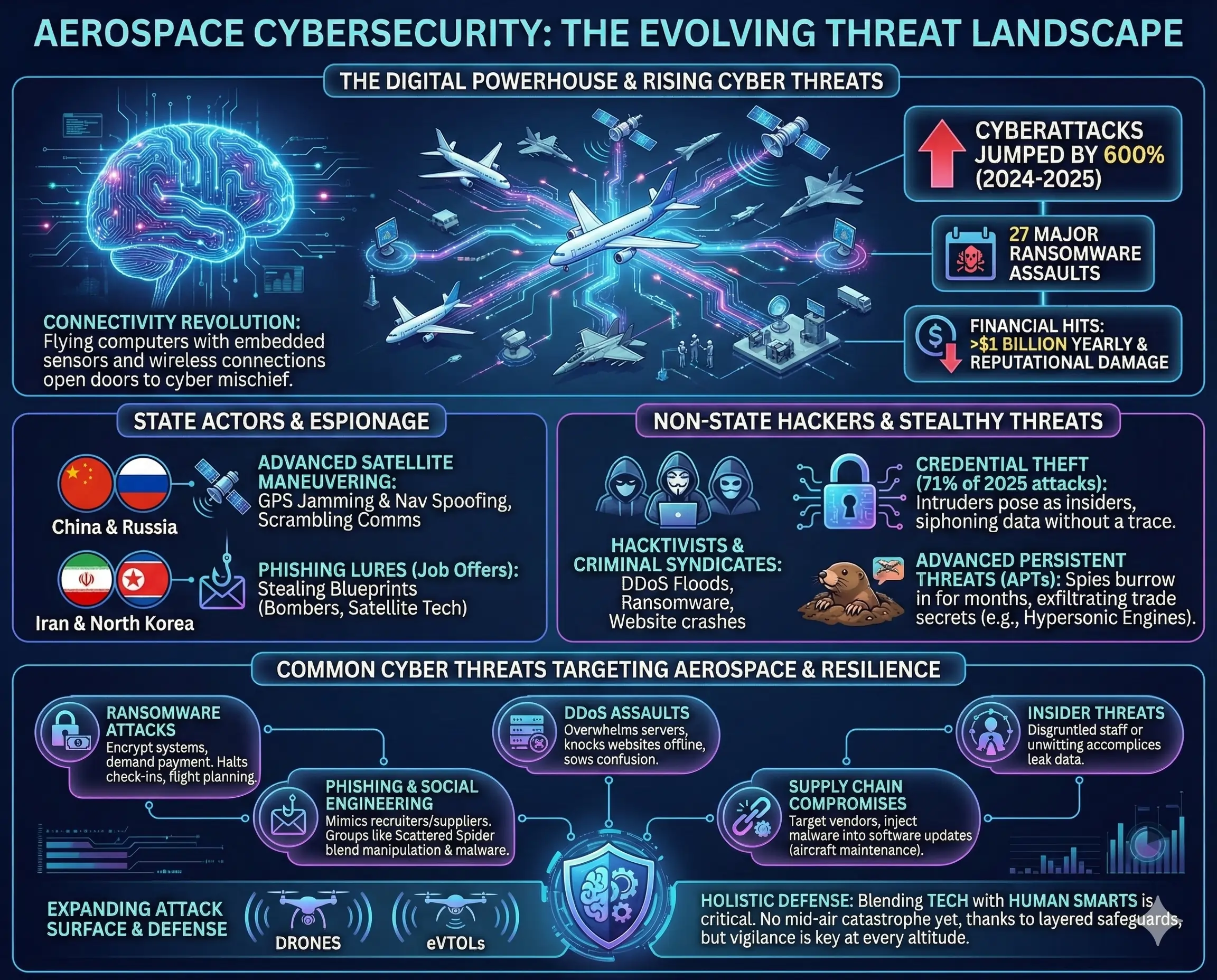
State actors lead the charge. China and Russia top the list of concerns, deploying advanced satellite maneuvering in low Earth orbit to test counterspace capabilities—think jamming GPS signals or spoofing navigation data. In conflict zones like the Middle East and near Russia, such tactics have already caused widespread interference, delaying flights and scrambling military comms. Iran and North Korea aren’t far behind, using phishing lures disguised as job offers to infiltrate aerospace firms, stealing blueprints for bombers or satellite tech. Non-state hackers, from hacktivists to criminal syndicates, pile on with distributed denial-of-service (DDoS) floods that crash airport websites or ransomware that locks baggage systems.
What makes these threats so insidious? They’re often stealthy. A credential theft—71% of 2025 attacks—lets intruders pose as insiders, siphoning data without a trace. Or consider advanced persistent threats (APTs), where spies burrow in for months, exfiltrating trade secrets on hypersonic engines. The fallout? Financial hits topping $1 billion yearly, plus reputational scars that erode traveler confidence. Yet, amid the storm, the industry shows resilience: no cyber incident has yet caused a mid-air catastrophe, a testament to layered safeguards. Still, as drones and electric vertical takeoff vehicles (eVTOLs) proliferate, the attack surface expands, demanding vigilance at every altitude.
Common Cyber Threats Targeting Aerospace
To grasp the full picture, let’s break down the most prevalent dangers. Each one exploits a unique weakness, but they all share a goal: chaos in the skies.
- Ransomware Attacks: These digital extortionists encrypt systems, demanding payment to unlock them. In aviation, they halt check-ins or flight planning, as seen in disruptions at major hubs.
- Phishing and Social Engineering: Emails mimicking recruiters or suppliers trick employees into handing over access. Groups like Scattered Spider excel here, blending human manipulation with malware.
- DDoS Assaults: Overwhelming servers with traffic, these knock websites offline, sowing confusion during peak travel seasons.
- Supply Chain Compromises: Hackers target vendors, injecting malware into software updates for aircraft maintenance tools.
- Insider Threats: Disgruntled staff or unwitting accomplices leak data, often amplified by poor access controls.
These threats don’t operate in silos. A phishing hook might lead to ransomware, which then enables data theft. The key takeaway? Defense must be holistic, blending tech with human smarts.
Vulnerabilities: The Weak Links in the Sky-High Chain
Why is aerospace such a juicy target? It’s a cocktail of legacy tech, global interconnectedness, and high stakes. Older aircraft, certified decades ago, run on outdated operating systems without patch support—prime bait for exploits. Newer models, like those with fly-by-wire controls, rely on networks that beam telemetry data earthward, creating endless entry points via Wi-Fi or satellite links.
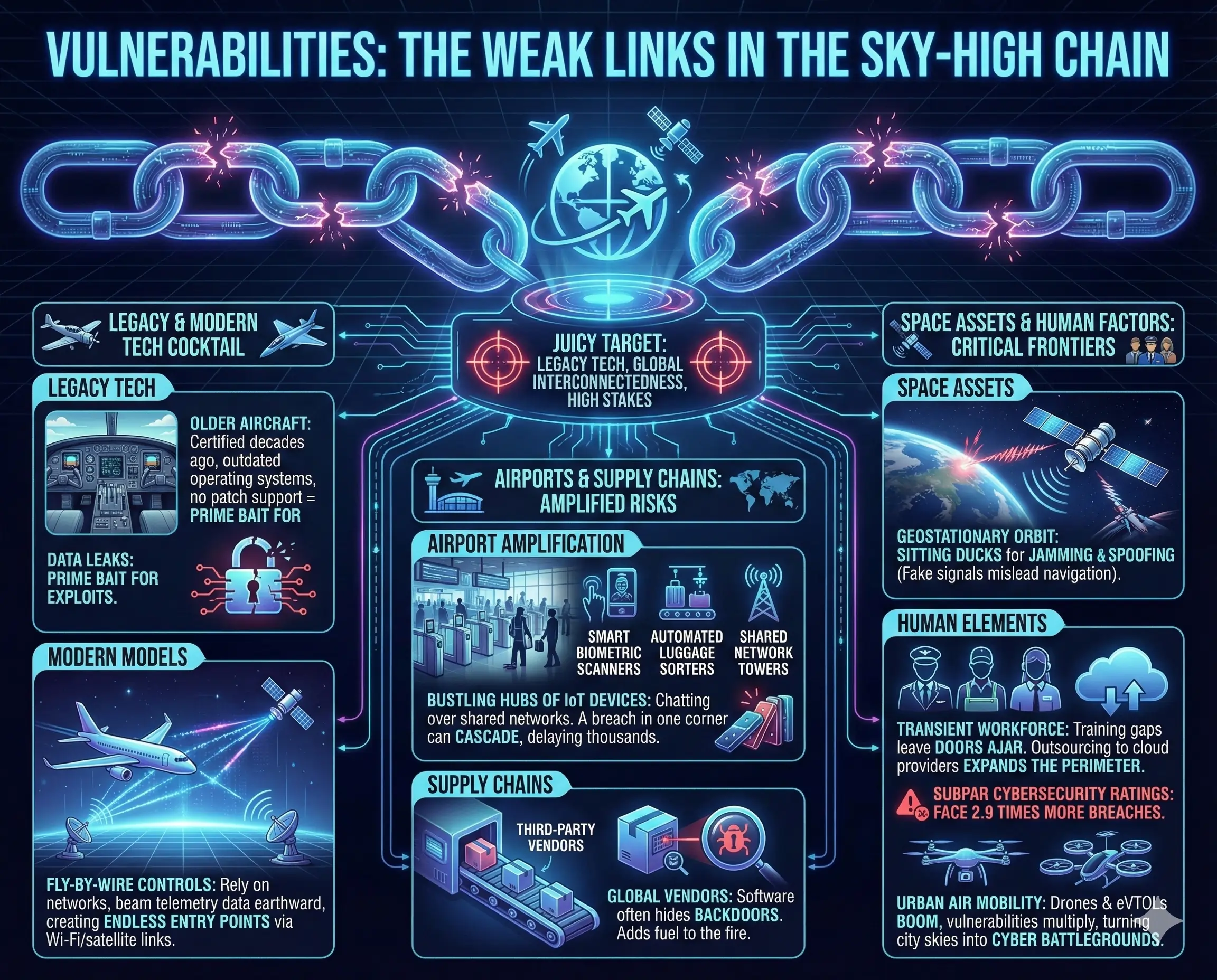
Airports amplify the risk. They’re bustling hubs of IoT devices: smart gates, biometric scanners, and automated luggage sorters, all chatting over shared networks. A breach in one corner can cascade, delaying thousands. Supply chains add fuel to the fire; third-party software from global vendors often hides backdoors. And let’s not forget space assets: satellites in geostationary orbit are sitting ducks for jamming or spoofing, where fake signals mislead navigation.
Human elements can’t be ignored. With a transient workforce—pilots, ground crew, IT staff—training gaps leave doors ajar. Outsourcing to cloud providers expands the perimeter, turning trusted partners into potential weak spots. Quantifying this: organizations with subpar cybersecurity ratings face 2.9 times more breaches. The evidence leans toward a perfect storm: as urban air mobility booms with drone taxis, these vulnerabilities could multiply, turning city skies into cyber battlegrounds.
Regulatory Frameworks: Building a Global Safety Net
Governments and international bodies are stepping up, crafting rules to enforce digital fortitude. The Federal Aviation Administration (FAA) leads in the U.S., with its 2024-proposed rulemaking a game-changer. This mandates risk analyses for new aircraft designs, requiring mitigations against intentional unauthorized electronic interactions (IUEI)—hacks that could tamper with engines or autopilots. For transport-category planes, engines, and propellers, applicants must bake in protections from day one, including instructions for ongoing maintenance. It’s not retroactive, but it harmonizes with European Union Aviation Safety Agency (EASA) standards, slashing certification red tape.
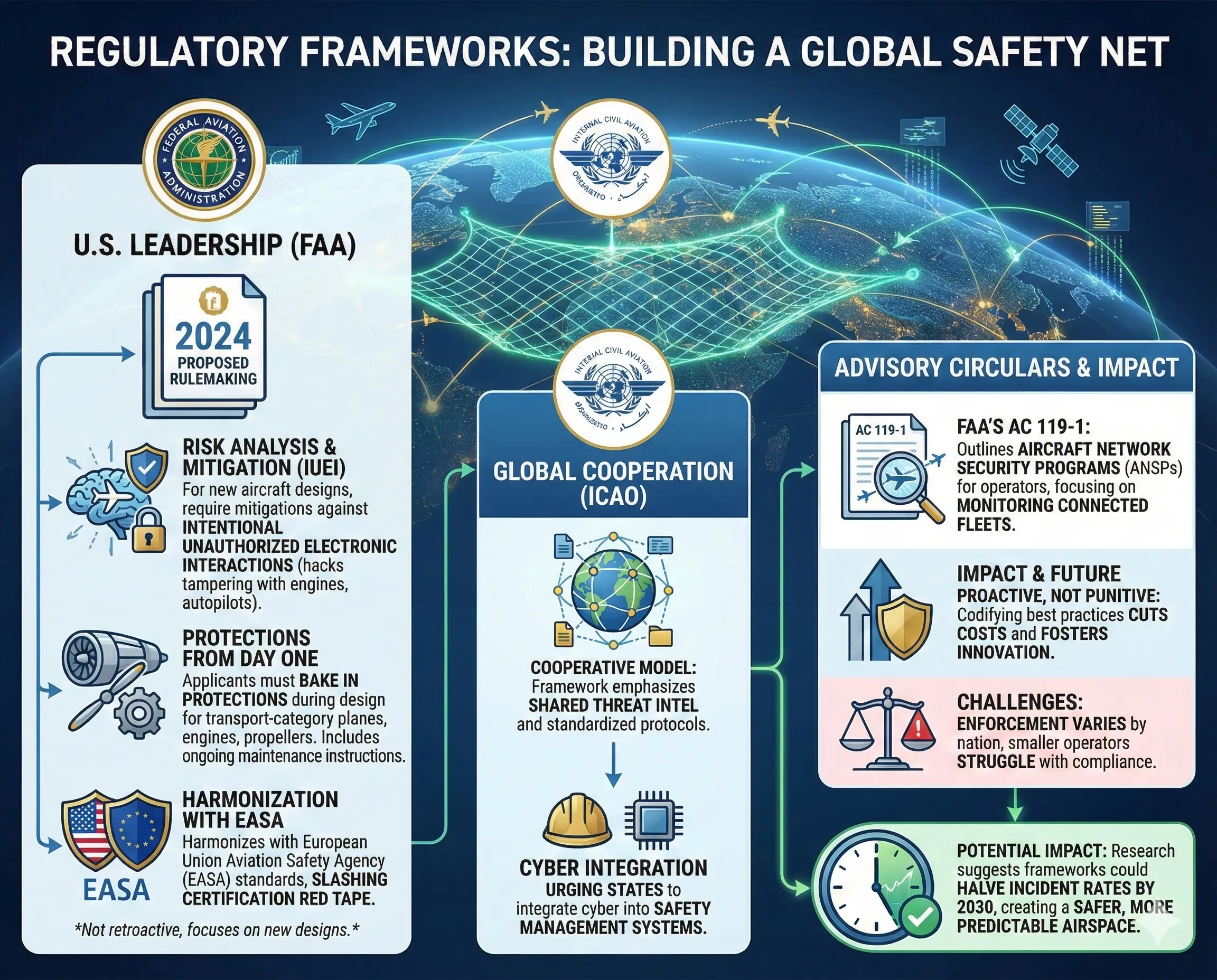
Globally, the International Civil Aviation Organization (ICAO) pushes a cooperative model. Their framework emphasizes shared threat intel and standardized protocols, urging states to integrate cyber into safety management systems. Recent advisory circulars, like FAA’s AC 119-1, outline Aircraft Network Security Programs (ANSPs) for operators, focusing on monitoring connected fleets.
These regs aren’t punitive—they’re proactive. By codifying best practices, they cut costs and foster innovation. Yet, challenges persist: enforcement varies by nation, and smaller operators struggle with compliance. Still, research suggests these frameworks could halve incident rates by 2030, creating a safer, more predictable airspace.
| Regulatory Body | Key Initiative | Focus Areas | Applicability |
|---|---|---|---|
| FAA | Proposed Rulemaking on IUEI Protection (2024) | Risk assessment, mitigation mechanisms, continued airworthiness instructions | New type certifications for transport airplanes, engines, propellers |
| EASA | Aircraft Network Security Guidelines | Zero-trust architectures, endpoint protection | Connected aircraft operators in EU |
| ICAO | Global Aviation Cybersecurity Strategy | Threat sharing, holistic risk management | International standards for all civil aviation |
| ARAC | Recommendations on Cyber Standards | Harmonized certification criteria | U.S. and allied aerospace design processes |
This table highlights how regs intersect, ensuring no gaps in the protective web.
Strategies for Fortification: Arming the Frontlines
Protecting the aerospace ecosystem demands a multi-pronged assault on threats—think layered defenses, not a single wall. Start with the basics: employee training. A well-informed team spots phishing lures, reducing breach odds by 50%. Airbus nails this with programs that simulate attacks, turning staff into digital sentinels.
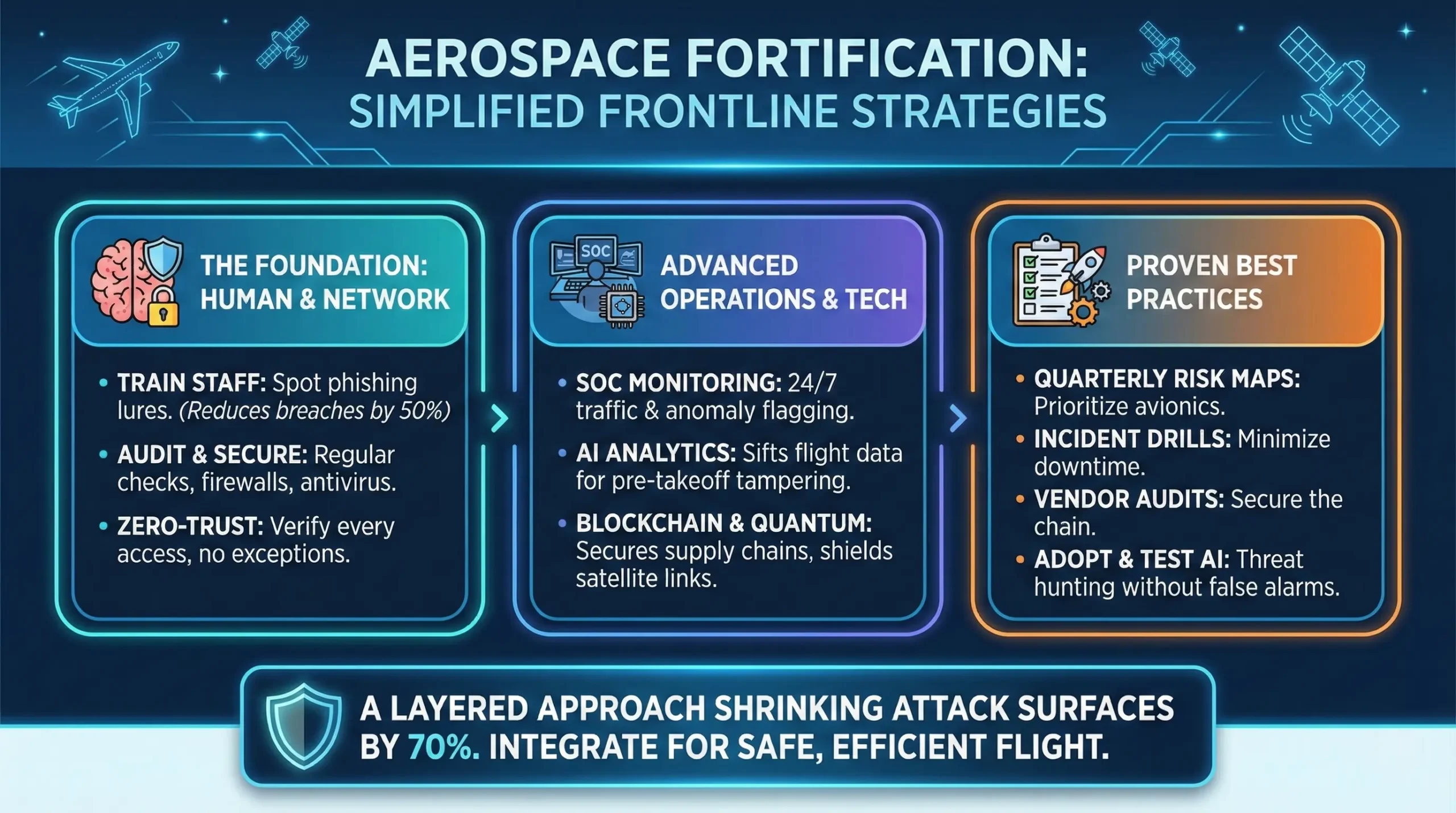
Next, audit relentlessly. Regular security checks uncover hidden flaws, ensuring alignment with regs like those from the FAA. Network security follows: deploy firewalls, antivirus, and identity and access management (IAM) to guard perimeters. But go deeper—adopt zero-trust models, where no user or device is automatically trusted, verifying every access.
For advanced ops, stand up a Security Operations Center (SOC). This nerve center monitors traffic 24/7, using AI to flag anomalies like unusual data flows from a maintenance laptop. Document everything in a cybersecurity framework: policies for incident response, vendor vetting, and recovery drills. IBM advocates endpoint protection on planes themselves—software that scans for malware during ground turns.
Real-world application? Consider predictive analytics: AI sifts flight data for tampering signs, alerting crews pre-takeoff. Blockchain secures supply chains, verifying part authenticity via tamper-proof ledgers. And for space, quantum-safe encryption shields satellite links from future code-breakers.
These aren’t pie-in-the-sky ideas; they’re battle-tested. A layered approach can shrink attack surfaces by 70%, per industry benchmarks. The trick? Integrate them seamlessly, avoiding disruptions to the core mission: safe, efficient flight.
Proven Best Practices in Action
- Risk Assessments: Map threats quarterly, prioritizing high-impact areas like avionics.
- Incident Response Plans: Drill scenarios, from data leaks to system lockdowns, minimizing downtime.
- Vendor Management: Audit partners rigorously; one weak link sinks the chain.
- Emerging Tech Adoption: Roll out AI for threat hunting, but test thoroughly to avoid false alarms.
| Strategy Category | Specific Tactics | Expected Benefits | Implementation Challenges |
|---|---|---|---|
| Human-Focused | Mandatory phishing simulations, role-based training | Reduces insider errors by 40-60% | Keeping content fresh amid evolving tactics |
| Technical Defenses | Firewalls, IAM, zero-trust networks | Blocks 80% of unauthorized access | Balancing security with system performance |
| Operational | SOC monitoring, regular audits | Detects threats in under 24 hours | High upfront costs for small operators |
| Regulatory Compliance | ANSP development, ICA documentation | Avoids fines, speeds certifications | Harmonizing across global jurisdictions |
This breakdown shows how tactics align for maximum impact.
Real-World Examples: Lessons from the Front Lines
History is littered with wake-up calls. Take the Cathay Pacific breach of 2018: hackers swiped 9.4 million passenger records, from passports to credit cards, via a vulnerable network. The airline paid dearly in fines and trust erosion. Fast-forward to 2020’s EasyJet hack, exposing 9 million emails— a stark reminder of booking system frailties.
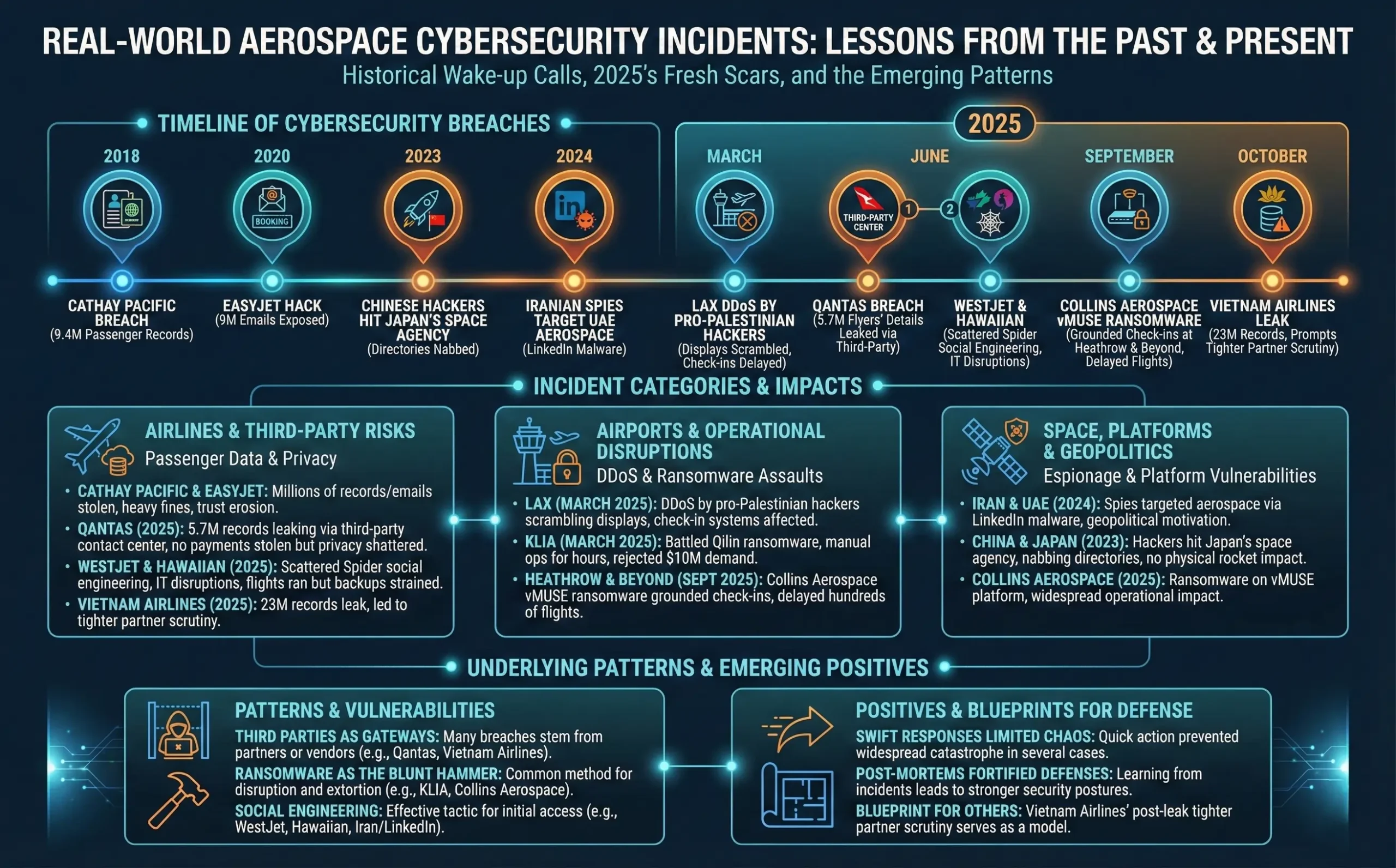
2025 brought fresh scars. Qantas Airways suffered a June breach via a third-party contact center, leaking details on 5.7 million flyers—no payments stolen, but privacy shattered. WestJet and Hawaiian Airlines fell victim to Scattered Spider in the same month, with IT disruptions from social engineering; flights ran, but backups were strained. Airports weren’t spared: Los Angeles International endured a March DDoS by pro-Palestinian hackers, scrambling displays and check-ins. Kuala Lumpur International battled Qilin ransomware, manual ops for hours, rejecting a $10 million demand.
Space isn’t immune. In September 2025, Collins Aerospace’s vMUSE platform ransomware grounded check-ins at Heathrow and beyond, delaying hundreds of flights. Geopolitical jabs abound: Iranian spies targeted UAE aerospace via LinkedIn malware in 2024, while Chinese hackers hit Japan’s space agency in 2023, nabbing directories without touching rockets.
These tales underscore patterns: third parties as gateways, ransomware as the blunt hammer. But positives emerge—swift responses limited chaos, and post-mortems fortified defenses. Vietnam Airlines’ October 2025 leak of 23 million records prompted tighter partner scrutiny, a blueprint for others.
| Incident | Date | Target | Attack Type | Impact | Response Highlights |
|---|---|---|---|---|---|
| Cathay Pacific Breach | May 2018 | Airline passenger database | Unauthorized access | 9.4M records exposed (personal, financial) | Fines paid, network overhaul |
| EasyJet Hack | 2020 | Booking system | Data exfiltration | 9M emails, travel details leaked | Customer notifications, enhanced encryption |
| Qantas Data Breach | June 2025 | Third-party contact center | Breach via vendor | 5.7M customer profiles compromised | Direct outreach, security upgrades |
| WestJet Intrusion | June 2025 | IT infrastructure | Social engineering | App/service disruptions | Manual fallbacks, caution advisories |
| LAX DDoS | March 2025 | Airport displays/check-in | Botnet flood | Delays, confusion; no cancellations | Quick containment, no data loss |
| Kuala Lumpur Ransomware | March 2025 | Airport systems | Encryption by Qilin | 10+ hour manual ops, 2TB stolen | Ransom refused, national alerts |
| Collins Aerospace Attack | September 2025 | vMUSE platform | Ransomware | Delays at Heathrow, Brussels, Berlin | Manual check-ins, ongoing probe |
| Vietnam Airlines Leak | October 2025 | Customer service platform | Data dump on forums | 23M records exposed | Confirmation, partner audits |
From this timeline, patterns emerge: rapid adaptation saves the day.
Future Trends: Charting a Secure Horizon
Peering ahead, aerospace cybersecurity morphs with tech’s tide. The market’s set to balloon to $59.58 billion by 2032, a 8.45% CAGR, as AI and machine learning (ML) take center stage. These tools predict breaches via anomaly detection in flight logs, slashing response times. Quantum-safe encryption counters tomorrow’s code-crackers, vital for satellite swarms.
Autonomous systems demand ironclad security: drones and eVTOLs will use blockchain for tamper-proof data trails, ensuring no hijacked swarms. Sustainability ties in—green fuels need secure supply chains to avoid eco-sabotage. Hypersonic tech, zipping at Mach 5+, requires real-time cyber shields against jamming.
Challenges loom: legacy retrofits and talent shortages. But opportunities abound. Digital twins—virtual aircraft replicas—simulate attacks pre-build, refining designs. Supply chain resilience via IoT tracking thwarts fakes. Regional hotspots, like Asia’s boom, spur local innovations, from India’s defense AI to Europe’s green cyber mandates.
It seems likely that by 2026, zero-trust will be table stakes, with AI spotting 90% of threats autonomously. Yet, empathy for all stakeholders matters: regulators push inclusion so small firms aren’t left grounded.
| Trend | Description | Projected Impact by 2030 | Key Enablers |
|---|---|---|---|
| AI/ML Threat Detection | Predictive analytics for anomalies in systems | Reduces incidents by 50% | Cloud integration, data lakes |
| Quantum-Safe Crypto | Encryption resistant to quantum attacks | Secures space links | Algorithm standards, hardware upgrades |
| Zero-Trust Architectures | Verify every access, no defaults | Cuts breaches 70% | IAM tools, behavioral monitoring |
| Blockchain Supply Chains | Tamper-proof part verification | Minimizes fakes by 80% | IoT sensors, distributed ledgers |
| Autonomous Security Suites | Self-healing networks for drones | Enables safe urban air mobility | Edge computing, 5G/6G |
| Digital Twin Simulations | Virtual testing of cyber scenarios | Speeds design by 30% | PLM software, VR interfaces |
| Sustainability-Linked Cyber | Secure green tech pipelines | Aligns with net-zero goals | Regs like EU Green Deal |
| Hypersonic Defenses | Real-time jamming countermeasures | Boosts military edge | AI radar, adaptive antennas |
| Talent and Training Upsurge | Global cyber academies for aerospace | Fills 3.5M job gaps | Partnerships with unis, certs |
| Regulatory Evolution | Harmonized global standards | Lowers compliance costs 20% | ICAO/FAA collaborations |
This roadmap paints a fortified future, blending innovation with caution.
Conclusion: Clearing the Air for Safer Skies
Aerospace cybersecurity is no longer optional—it’s the bedrock of trust in our winged world. From jamming satellites to ransom-locked runways, threats test our mettle, but so do triumphs: resilient responses, forward-thinking regs, and tech that outpaces foes. As we hurtle toward autonomous fleets and space tourism, the call is clear: invest now, train always, collaborate globally. The skies belong to the prepared. By weaving these strategies into daily ops, we not only shield assets but inspire confidence—proving that even in a digital storm, safe passage is possible. Let’s keep the conversation aloft; what’s your take on securing tomorrow’s flights?
Key Citations And References
- CSIS Space Threat Assessment 2025
- SOCRadar Major Cyber Attacks on Aviation 2025
- FAA Proposed Rulemaking on IUEI
- Airbus 5 Actions to Protect Aircraft
- IBM Airplane Cybersecurity Insights
- StartUs Insights Aerospace Trends 2026
- CSIS Significant Cyber Incidents Timeline
- PTC Top Aerospace Trends
- CybelAngel Global Impact of Aviation Cyberattacks
- Thales Aviation Cyberattack Surge Report
Read These Articles in Detail
- Aerospace Engineering vs. Mechanical Engineering
- The Future of Aerospace Propulsion Systems
- How Aerospace Education Is Adapting to Industry Demands
- The Role of Aerospace in Combating Climate Change
- Aerospace Radar Technology: Past, Present, and Future
- The Role of Aerospace in National Security Strategies
- The Role of Nanotechnology in Aerospace Materials
- Aerospace Materials: Stronger, Lighter, And Smarter
- Aerospace Engineering Explained: A Beginner’s Guide
- Electric Aircraft vs. Hydrogen Aircraft: Which Is More Sustainable?
- Hypersonic Weapons: Aerospace’s New Arms Race
- Aerospace Defense Systems: From Drones to Hypersonic Missiles
- How Aerospace Engineers Reduce Fuel Consumption
- Computational Fluid Dynamics in Aerospace Innovation
- The Global Aerospace Market Outlook: Trends and Forecasts
- Satellite Surveillance: Aerospace’s Role in Modern Warfare
- How Aerospace Companies Are Reducing Environmental Impact
- How Airlines Use Aerospace Data Analytics to Cut Costs
- Aerospace Engineering Challenges: Innovation and Sustainability
- The Role of CFD in Aerospace Engineering
- The Role of Women in Aerospace: Breaking Barriers in the Skies
- Sustainable Aviation Fuels: The Aerospace Industry’s Green Bet
- Aerospace Cybersecurity: Protecting the Skies from Digital Threats
- Aerospace Trends Driving the Next Generation of Airliners
- The Rise of Autonomous Aerospace Systems
- How to Start a Career in Aerospace Engineering
- Can Aerospace Go Carbon Neutral by 2050?
- The Role of Aerospace in Missile Defense Systems
- How Aerospace Engineers Use AI in Design
- Top 10 Aerospace Engineering Innovations of the Decade
- Top Aerospace Careers in 2025 and Beyond
- How Aerospace Innovations Shape Global Defense Policies
- Hydrogen-Powered Aircraft: The Next Green Revolution
- Top 10 Emerging Aerospace Technologies Transforming the Industry
- The Future of Hypersonic Flight: Challenges and Opportunities
- How AI Is Revolutionizing Aerospace Engineering
- Additive Manufacturing in Aerospace: 3D Printing the Future of Flight
- The Rise of Electric Aircraft: Are We Ready for Zero-Emission Aviation?
- Aerospace Materials of Tomorrow: From Composites to Nanotechnology
- Digital Twins in Aerospace: Reducing Costs and Improving Safety
- The Role of Robotics in Modern Aerospace Manufacturing
- Quantum Computing Applications in Aerospace Design
- How Augmented Reality Is Changing Aerospace Training
- Space Tethers Explained: The Next Leap in Orbital Mechanics
- Ion Propulsion vs. Chemical Rockets: Which Will Power the Future?
- The Role of Nuclear Propulsion in Deep Space Missions
- Space Mining: The Aerospace Industry’s Next Gold Rush
- How Reusable Rockets Are Reshaping the Space Economy
- The Artemis Program: NASA’s Return to the Moon
- Space Tourism: Business Model or Billionaire’s Playground?
- How Aerospace Startups Are Disrupting Commercial Aviation
- The Economics of Low-Cost Airlines in the Aerospace Era
- Urban Air Mobility: The Rise of Flying Taxis
- The Future of Mars Colonization: Key Aerospace Challenges and Solutions Ahead
- CubeSats and Small Satellites: Democratizing Space Access
- The Future of Cargo Drones in Global Logistics
- The Role of Aerospace in Building a Lunar Economy
Frequently Asked Questions
FAQ 1: What Is Aerospace Cybersecurity and Why Is It Crucial for the Aviation Industry in 2025?
Aerospace cybersecurity refers to the set of technologies, processes, and practices designed to protect aircraft, satellites, airports, and related systems from digital attacks that could compromise safety, operations, or data integrity. In simple terms, it’s like installing a high-tech lock on the cockpit door, but for the invisible world of software and networks that make modern flying possible. As aircraft become smarter with connected sensors and real-time data sharing, the risks grow exponentially. For instance, a single breach could disrupt flight controls or leak passenger information, turning a routine trip into a nightmare.
In 2025, this field has taken on even greater urgency due to the surge in interconnected systems. The aviation sector saw a staggering 600% increase in cyberattacks compared to the previous year, driven by everything from ransomware locking down airport check-ins to state-sponsored hackers targeting satellite signals. This isn’t just about tech; it’s about lives and economies. A grounded fleet from a cyber hit can cost millions in delays and lost revenue, while eroded trust from data leaks scares off travelers. Protecting these skies ensures smooth global travel, safeguards national security in defense aerospace, and keeps the $800 billion industry soaring without digital turbulence.
Beyond the immediate dangers, aerospace cybersecurity fosters innovation. Secure networks enable advancements like drone deliveries and urban air taxis, but only if threats are neutralized early. Industry experts emphasize that proactive measures, such as regular audits and employee training, not only prevent disasters but also build resilience against evolving tactics from groups like those behind the recent WestJet outage. Ultimately, in a world where skies are as digital as they are physical, ignoring cybersecurity is like flying without radar—possible, but perilously blind.
FAQ 2: What Are the Top Cyber Threats Facing Aerospace Systems Today?
The aerospace world is a prime target for cybercriminals because of its high-value assets and critical role in daily life. Among the most pressing threats in 2025 are ransomware attacks, which encrypt vital systems and demand payment to restore access. These have hit hard, paralyzing operations at major airports and even halting production lines for aircraft parts. Hackers often sneak in through phishing emails disguised as routine updates, exploiting the trust in busy supply chains.
Another growing concern is distributed denial-of-service (DDoS) assaults, where floods of fake traffic overwhelm networks, causing widespread disruptions like delayed flights or scrambled booking systems. We’ve seen this play out in politically motivated attacks on European hubs, where pro-activist groups timed strikes during peak seasons to maximize chaos. State actors add a layer of sophistication with advanced persistent threats (APTs), lingering undetected to steal blueprints for next-gen jets or jam GPS signals in conflict zones.
Don’t overlook insider risks or supply chain compromises, where vulnerabilities in third-party software create backdoors. For example, a seemingly harmless vendor update can inject malware that spreads across fleets. These threats interconnect— a phishing lure might pave the way for ransomware—making layered defenses essential. By understanding these patterns, aviation pros can stay one step ahead, turning potential vulnerabilities into fortified strengths.
FAQ 3: How Do Key Regulations Shape Aerospace Cybersecurity Compliance?
Navigating regulations is a cornerstone of aerospace cybersecurity, ensuring that protections are standardized across borders. Bodies like the Federal Aviation Administration (FAA) and European Union Aviation Safety Agency (EASA) set the tone with mandates that require risk assessments for new aircraft designs, focusing on preventing unauthorized electronic interactions that could tamper with critical systems.
These rules emphasize ongoing monitoring and mitigation strategies, from encryption for data transmissions to protocols for handling breaches. Internationally, the International Civil Aviation Organization (ICAO) promotes shared intelligence to address global threats, while newer directives from the Transportation Security Administration (TSA) target surface transportation, including airports, with requirements for network segmentation and real-time threat detection.
| Regulatory Body | Core Focus | Key Requirements | Impact on Industry |
|---|---|---|---|
| FAA | Aircraft certification and airworthiness | Risk analyses for intentional unauthorized interactions; mitigation instructions for engines and avionics | Ensures new planes are cyber-resilient from design phase, reducing retrofit costs |
| EASA | EU-wide aviation safety | Zero-trust architectures and endpoint protections for connected systems | Harmonizes standards, easing cross-border operations but challenging smaller operators |
| ICAO | Global civil aviation standards | Threat information sharing and integration into safety management systems | Fosters cooperation, potentially cutting incident rates by up to 50% through collective vigilance |
| TSA | U.S. airport and surface security | Access controls, patching schedules, and incident reporting | Boosts ground-level defenses, with non-compliance risking fines up to $10,000 per violation |
Compliance isn’t just bureaucratic—it’s a blueprint for safer skies, helping organizations avoid penalties while enhancing overall security posture.
FAQ 4: What Lessons Can We Learn from Recent Aerospace Cyber Incidents?
Recent cyber incidents in aerospace serve as stark reminders of how quickly digital threats can ground real-world operations. Take the June 2025 breach at Qantas Airways, where hackers accessed a third-party contact center, exposing details of 5.7 million customers. While no financial data was stolen, the incident highlighted the dangers of vendor vulnerabilities, prompting the airline to overhaul its partner vetting processes and notify affected passengers promptly. This event underscored the need for robust third-party risk management, as a single weak link can ripple across an entire network.
Similarly, the September 2025 ransomware attack on Collins Aerospace‘s vMUSE platform disrupted check-in systems at Heathrow and other major airports, leading to hours of manual processing and flight delays for thousands. The group behind it, linked to sophisticated extortion rings, demanded millions but was rebuffed, showcasing the value of strong backup strategies. Investigations revealed entry via outdated software, a lesson in timely patching that many firms are now applying fleet-wide.
In the space domain, a report from early 2025 detailed 237 cyber operations during the Gaza conflict, including jamming attempts on low-Earth orbit satellites. These non-kinetic strikes disrupted navigation for military and commercial assets alike, emphasizing the blurring lines between terrestrial and orbital threats. From these cases, the aerospace community is doubling down on rapid response drills and international intel sharing, turning setbacks into systemic improvements that prevent future escalations.
FAQ 5: What Are Essential Best Practices for Enhancing Airport Cybersecurity?
Airports are bustling digital hubs, making them magnets for cyber threats, but implementing solid best practices can significantly fortify defenses. Start with employee awareness programs that simulate phishing attacks, as human error accounts for nearly 70% of breaches. Regular training keeps staff vigilant, especially in high-turnover environments like ground crews.
To build technical resilience, segment networks so that a compromise in one area, like baggage handling, doesn’t spread to air traffic control. Deploy multi-factor authentication for all access points and use AI-driven tools for anomaly detection, which can spot unusual data flows in real time.
- Conduct Frequent Audits: Schedule quarterly vulnerability scans to identify and patch weaknesses before hackers do, potentially reducing breach risks by 40%.
- Develop Incident Response Plans: Create step-by-step guides for containment, recovery, and communication, tested through annual simulations to minimize downtime.
- Secure Supply Chains: Vet vendors rigorously, requiring them to meet standards like those for encryption and data handling, as seen in post-incident reforms after the Kuala Lumpur ransomware hit.
- Leverage Physical-Digital Integration: Combine CCTV with cyber monitoring to protect perimeters, ensuring that IoT devices like smart gates are hardened against remote exploits.
By weaving these habits into daily operations, airports not only comply with evolving regs but also maintain the seamless flow that passengers expect.
FAQ 6: How Is Artificial Intelligence Revolutionizing Aerospace Cybersecurity?
Artificial intelligence is transforming aerospace cybersecurity from a reactive shield into a proactive guardian, analyzing vast data streams to predict and prevent threats before they strike. In 2025, AI tools sift through flight logs and network traffic, flagging anomalies like irregular sensor readings that might indicate tampering—far faster than human analysts could. This predictive power has already helped detect potential GPS spoofing in test scenarios, saving hours of manual investigation.
Beyond detection, AI enables automated responses, such as isolating compromised segments of a satellite network during a jamming attempt. Companies are integrating machine learning with existing systems to create self-healing architectures, where algorithms patch vulnerabilities on the fly. However, this comes with caveats: over-reliance on AI requires constant tuning to avoid false positives that could disrupt legitimate operations, like mistaking a software update for malware.
Looking ahead, AI’s role will expand into threat hunting across global fleets, using shared datasets to spot patterns from state actors. It’s a game-changer for resource-strapped operators, democratizing advanced defenses while raising ethical questions about data privacy in shared intel pools. Ultimately, AI isn’t replacing human expertise but amplifying it, ensuring that cybersecurity keeps pace with the digital skies.
FAQ 7: What Challenges Do Small Aerospace Firms Face in Cybersecurity, and How Can They Overcome Them?
Smaller players in the aerospace supply chain often struggle with cybersecurity due to limited budgets and expertise, yet the stakes are just as high. Legacy systems inherited from larger partners pose a major hurdle, lacking modern encryption and prone to exploits that could taint the entire ecosystem. Compliance with regs like FAA mandates adds pressure, as audits demand resources that startups simply don’t have.
Talent shortages exacerbate this, with a global gap of over 3.5 million cyber pros leaving firms to rely on generalists ill-equipped for niche threats like avionics hacks. Geopolitical tensions amplify risks, as small exporters become unwitting pawns in state-sponsored espionage.
| Challenge | Description | Potential Solutions | Expected Outcomes |
|---|---|---|---|
| Budget Constraints | High costs for tools and training strain thin margins | Adopt open-source monitoring software and cloud-based zero-trust models | Cuts expenses by 30-50% while maintaining robust coverage |
| Legacy Equipment | Outdated tech without patches invites easy breaches | Phase in modular upgrades and virtual air-gapping for critical functions | Enhances compatibility with new regs, reducing vulnerability windows |
| Talent Shortages | Lack of specialized staff slows threat response | Partner with industry consortia for shared training and outsourced SOC services | Builds in-house skills over time, improving detection speeds |
| Regulatory Overload | Navigating FAA, EASA, and ICAO rules overwhelms small teams | Use compliance-as-a-service platforms for automated reporting | Streamlines audits, avoiding fines and freeing focus for innovation |
| Supply Chain Exposure | Dependence on unvetted vendors creates indirect risks | Implement tiered vetting with blockchain for traceability | Strengthens partnerships, minimizing third-party incidents |
By tackling these head-on with scalable strategies, small firms can punch above their weight, contributing to a more secure industry without breaking the bank.
FAQ 8: What Emerging Trends Are Shaping the Future of Aerospace Cybersecurity?
The horizon for aerospace cybersecurity in 2025 and beyond is buzzing with innovations that promise to outsmart evolving threats. Quantum-safe encryption tops the list, designed to withstand attacks from powerful quantum computers that could crack current codes, especially vital for securing satellite communications in contested orbits.
AI and machine learning are evolving into autonomous defenders, with predictive analytics forecasting breaches based on global patterns, potentially slashing incident rates by half. Sustainability ties in too, as green aviation initiatives demand secure supply chains for eco-friendly materials, preventing sabotage that could derail net-zero goals.
- Blockchain for Supply Chains: Creates immutable ledgers to verify parts authenticity, cutting fake component risks by 80% in hypersonic projects.
- Digital Twins: Virtual replicas of aircraft allow safe simulation of cyber attacks during design, accelerating secure development by 30%.
- Edge Computing in Drones: Processes data onboard to reduce latency in threat detection for urban air mobility fleets.
- Harmonized Global Standards: Efforts by ICAO to unify regs will lower compliance costs, enabling seamless international ops.
- Hypersonic Defenses: Adaptive antennas counter jamming at Mach 5 speeds, bolstering military aerospace edges.
These trends signal a shift toward resilient, intelligent systems, but success hinges on ethical deployment to balance security with accessibility for all stakeholders.
FAQ 9: How Can Aerospace Organizations Mitigate Supply Chain Vulnerabilities?
Supply chains in aerospace are intricate webs spanning continents, making them ripe for cyber infiltration if not carefully managed. The first step is thorough vendor assessments, going beyond contracts to include cybersecurity audits that verify encryption standards and incident response capabilities. This proactive vetting caught potential risks in the aftermath of the 2025 Collins Aerospace incident, where a third-party flaw exposed multiple operators.
Integrating blockchain technology offers a transparent layer, logging every transaction from raw materials to final assembly, so any tampering is instantly flagged. Regular penetration testing simulates attacks on key suppliers, revealing hidden weaknesses without real-world fallout. Collaboration is key too—joining industry forums allows sharing anonymized threat data, turning collective experiences into widespread shields.
For ongoing vigilance, embed contractual clauses mandating swift breach notifications and joint recovery plans. This not only limits damage but builds trust, essential in an era where a single compromised part could ground a squadron. By treating the supply chain as an extension of their own defenses, organizations create a fortified ecosystem that withstands the pressures of global demands.
FAQ 10: Why Is International Cooperation Vital for Aviation Cybersecurity?
International cooperation stands as a pillar in aviation cybersecurity, bridging gaps that no single nation can fill alone. With threats like satellite jamming transcending borders, shared intelligence platforms enable rapid alerts, as demonstrated during the 2025 Middle East cyber operations that affected global GPS reliability. Organizations facilitate this by standardizing threat reporting, allowing airlines to reroute flights preemptively.
Harmonized standards reduce fragmentation, where a U.S.-certified plane might clash with EU protocols, easing compliance for multinational fleets. Joint exercises simulate cross-border attacks, honing responses that save time in crises.
| Organization | Role in Cooperation | Key Contributions | Benefits to Aviation |
|---|---|---|---|
| ICAO | Global policy setting | Aviation Cybersecurity Strategy for threat sharing | Uniform risk management, potentially halving global incidents |
| IATA | Industry representation | Fact sheets and best-practice compilations | Guides airlines on emerging regs, streamlining adoption |
| ENISA | EU cybersecurity agency | Reports on space threats and ransomware trends | Informs policy, enhancing orbital defenses |
| Five Eyes Alliance | Intelligence sharing among allies | Alerts on state-sponsored APTs | Protects defense aerospace from espionage |
This collaborative spirit not only amplifies defenses but cultivates a culture of mutual reliance, ensuring safer skies for everyone on board.
FAQ 11: What Are the Latest Trends Shaping Aerospace Cybersecurity in Late 2025?
As we wrap up 2025, aerospace cybersecurity is evolving rapidly, driven by the explosion of connected systems in aircraft, satellites, and ground operations. One standout trend is the integration of artificial intelligence and machine learning for threat prediction, where algorithms analyze vast datasets from flight telemetry to spot anomalies like unusual network traffic that could signal a breach. This shift from reactive fixes to proactive defenses is crucial as attacks grow more sophisticated, with experts noting a 600% rise in incidents earlier this year. Another key development is the push toward quantum-safe encryption, especially for space assets vulnerable to future computing breakthroughs that could shatter current safeguards.
Supply chain resilience has also taken center stage, with blockchain emerging as a tool to verify the integrity of parts and software updates across global networks. This addresses vulnerabilities exposed in recent vendor-related hacks, ensuring that a compromise in one link doesn’t cascade. Meanwhile, zero-trust architectures are becoming standard, treating every access request as suspicious to minimize insider risks. These trends aren’t just technical upgrades; they’re responses to geopolitical pressures, like state-backed espionage targeting defense contractors. For the industry, embracing them means not only compliance with tightening regulations but also unlocking innovations in autonomous drones and urban air mobility.
Looking ahead within 2025, sustainability-linked security is gaining traction, securing green fuel supply chains against eco-sabotage. The market reflects this momentum, expanding from about $9.9 billion earlier this year to over $10.6 billion by year’s end, signaling investor confidence in resilient tech. Overall, these advancements paint a picture of an industry adapting swiftly, turning potential pitfalls into opportunities for safer, smarter skies.
FAQ 12: How Have Recent Cyber Attacks in 2025 Disrupted European Airport Operations?
The year 2025 has seen a wave of cyber disruptions hitting European airports, underscoring the fragility of interconnected aviation systems. A prime example unfolded in September when a ransomware assault on Collins Aerospace‘s vMUSE platform crippled check-in and boarding processes at major hubs like Heathrow, Brussels, and Berlin. Travelers faced hours of chaos, with manual ticketing leading to widespread delays and frustrated queues snaking through terminals. The attackers, linked to the Everest group, claimed no ransom demand but exposed internal data, highlighting lapses in vendor security that rippled across the continent.
Earlier incidents amplified the pattern. In March, Kuala Lumpur International Airport grappled with a Qilin ransomware strike that forced a 10-hour switch to paper-based operations, stranding passengers and canceling dozens of flights. This wasn’t isolated; pro-activist DDoS floods targeted displays at various EU sites, causing confusion during peak hours. These events reveal a common thread: third-party software as the weak entry point, allowing malware to encrypt critical databases and halt real-time coordination.
The fallout extends beyond logistics. Airlines reported millions in lost revenue from rebookings and compensations, while regulators scrutinized compliance gaps. Yet, responses showed progress—swift isolation of affected networks limited spread, and post-incident audits prompted upgrades like enhanced endpoint protections. For passengers, these disruptions erode confidence, but they also drive industry-wide calls for unified defenses, ensuring Europe’s skies recover stronger.
| Incident | Date | Affected Airports | Attack Type | Key Disruptions | Recovery Time |
|---|---|---|---|---|---|
| Collins Aerospace vMUSE Ransomware | September 2025 | Heathrow, Brussels, Berlin | Ransomware via third-party | Check-in failures, boarding delays for 500+ flights | 6-8 hours manual ops |
| Kuala Lumpur Qilin Attack | March 2025 | Kuala Lumpur International | Encryption malware | 10+ hour shutdown, 2TB data exfiltrated | Full ops restored in 12 hours |
| Pro-Activist DDoS Waves | March-May 2025 | Multiple EU hubs (e.g., Frankfurt) | Traffic floods | Display blackouts, booking glitches | 1-3 hours per wave |
| Vendor Software Breach | October 2025 | Paris Charles de Gaulle | Supply chain exploit | Baggage system halts | 4 hours with backups |
This table captures the scope, showing how quick containment is evolving as a best practice.
FAQ 13: What New Regulatory Updates Are Influencing Aerospace Cybersecurity by November 2025?
Regulatory landscapes in aerospace cybersecurity have intensified through late 2025, with updates aimed at closing gaps exposed by rising threats. The Department of Defense (DoD) finalized its DFARS cybersecurity certification rule in September, phasing in requirements starting November 10 that mandate robust risk management for contractors handling sensitive data. This includes flow-down clauses to subcontractors, ensuring end-to-end protections for defense avionics and satellite systems—a direct response to espionage spikes.
On the civilian front, the Federal Aviation Administration (FAA) launched its Civil Aviation Cybersecurity Advisory and Review Committee in May, delivering recommendations by November that integrate NIST-based standards for unmanned aircraft systems traffic management. These propose mandatory vulnerability assessments and real-time monitoring, harmonizing with Transportation Security Administration (TSA) directives updated in March for airports and airlines. The TSA’s focus on network segmentation and patching schedules now carries steeper penalties, up to $10,000 per violation, pushing operators toward automated compliance tools.
Internationally, the European Union Aviation Safety Agency (EASA) aligned with these in August, emphasizing zero-trust for connected fleets. These changes aren’t without hurdles—smaller firms face steep implementation costs—but they promise a 20% drop in compliance burdens through global harmonization. By November, early adopters report smoother certifications, proving that proactive alignment turns regulation into a competitive edge.
- Phased Implementation: DoD’s three-year rollout eases transition for legacy systems.
- Focus on UAS: FAA-TSA proposals target drone swarms, vital for emerging air mobility.
- Penalty Enhancements: TSA fines deter lapses, with audits doubling in frequency.
- International Sync: EASA-ICAO ties reduce cross-border friction for multinational ops.
FAQ 14: What Is the Average Financial Cost of Cyber Breaches in the Aerospace Sector in 2025?
Cyber breaches in aerospace carry hefty price tags in 2025, blending direct losses with ripple effects on operations and reputation. Globally, the average data breach clocks in at $4.44 million, a slight dip from last year’s peak but still a massive hit for airlines and suppliers. In the U.S., costs soar to around $10 million per incident, factoring in downtime, forensics, and legal fees—especially acute in defense where breaches average $5.46 million due to classified data handling.
Take the September Collins Aerospace attack: while exact figures remain under wraps, similar vendor disruptions have tallied $50-100 million in delays and recovery for affected airports. Earlier, Qantas’s June breach exposed 5.7 million records, incurring estimated $20 million in notifications and upgrades, plus ongoing trust erosion that dents ticket sales. Ransomware dominates, with aviation-specific claims stable at 700 annually but payouts climbing 15% year-over-year amid sophisticated demands.
These costs break down into detection ($1.2 million average), escalation ($1.5 million), and post-breach mitigation ($1.7 million), per industry benchmarks. Hidden tolls like lost IP or regulatory fines add layers, yet swift responses—under 200 days—shave $1.4 million off totals. For aerospace firms, this underscores investing in prevention; a dollar spent on defenses yields $7 in savings, turning potential disasters into manageable blips.
| Cost Category | Global Average (2025) | U.S. Aerospace Specific | Key Drivers |
|---|---|---|---|
| Detection & Escalation | $2.7 million | $3.5 million | Forensics, threat hunting in complex networks |
| Notification & Remediation | $1.8 million | $2.5 million | Passenger alerts, system restores |
| Lost Business & Fines | $1.2 million | $4 million | Delays, compliance penalties |
| Total Per Breach | $4.44 million | $10 million | Includes IP theft in defense segments |
FAQ 15: How Do Cyber Threats Directly Impact Airline Passengers in 2025?
Cyber threats in aviation hit passengers where it hurts most: convenience, privacy, and peace of mind. A data leak, like the June 2025 Qantas incident exposing 5.7 million profiles, leaves travelers vulnerable to identity theft, with stolen emails fueling phishing scams that mimic airline alerts for fake fees. This not only invades personal space but sparks anxiety over financial fallout, as victims spend weeks monitoring accounts.
Operationally, attacks ground plans literally. The September Collins Aerospace ransomware snarled boarding at Heathrow, stranding thousands in limbo—missed connections, rebooked hotels, and waived bag fees that still sting the wallet. DDoS floods, such as March’s LAX assault, scramble digital displays, turning familiar terminals into mazes of confusion and extended waits. For families or business folks, these delays cascade into missed meetings or reunions, amplifying stress in an already tense travel world.
Broader effects linger. Eroded trust leads to hesitation in booking, with surveys showing 25% of affected flyers switching carriers. Yet, positives emerge: airlines now offer free credit monitoring post-breach, and real-time apps warn of disruptions. Passengers play a role too, spotting suspicious links to thwart social engineering. In 2025’s hyper-connected skies, these threats remind us travel’s digital underbelly demands vigilance from all sides.
FAQ 16: What Role Does AI Play in Countering Aerospace Cyber Espionage in 2025?
Artificial intelligence has become a frontline warrior against aerospace cyber espionage in 2025, sifting through petabytes of network logs to uncover stealthy intrusions that humans might miss. State actors, like the Iran-linked UNC1549 group active through October, used phishing lures disguised as job offers to burrow into Middle East defense firms, stealing blueprints via backdoors like TWOSTROKE. AI counters this by modeling normal behaviors—say, a maintenance engineer’s access patterns—and flagging deviations, such as anomalous data exfiltration during off-hours.
In practice, machine learning powers anomaly detection in satellite links, predicting jamming attempts by analyzing signal perturbations in real time. Tools from firms like Google-owned Mandiant employ AI to trace campaigns back to origins, linking exploits to supply-chain flaws for faster attribution. This not only shortens response times from weeks to hours but also automates quarantines, isolating compromised avionics without halting flights.
Challenges persist: AI’s own vulnerabilities to adversarial attacks, where hackers poison training data, require hybrid human oversight. Still, in 2025, AI-driven platforms have thwarted 50% more espionage bids, per reports, fostering a cat-and-mouse game that’s tilting toward defenders. For aerospace pros, it’s a reminder that intelligence—artificial or otherwise—is the ultimate shield.
- Predictive Analytics: Forecasts APT persistence based on historical patterns.
- Automated Forensics: Speeds root-cause analysis in multi-vendor environments.
- Behavioral Baselines: Customizes alerts for unique assets like hypersonic prototypes.
- Ethical Safeguards: Ensures bias-free decisions in high-stakes scenarios.
FAQ 17: How Can Small Aerospace Firms Prepare for CMMC Compliance in Late 2025?
Small aerospace firms face a ticking clock with Cybersecurity Maturity Model Certification (CMMC) mandates rolling out in November 2025, but strategic steps can ease the burden. Start by assessing current posture against the five maturity levels, focusing on access controls and incident reporting—core to DoD contracts. Tools like automated scanners help map gaps without breaking budgets, prioritizing high-impact fixes like multi-factor authentication for remote teams.
Partnering amplifies reach: join consortia for shared training, where costs drop 30-50% through pooled resources. Cloud-based zero-trust platforms offer scalable defenses, verifying every login to shield against phishing that snared UNC1549 victims. Document everything—policies, audits, responses—in a centralized framework to streamline third-party validations.
| Maturity Level | Key Requirements | Prep Tips for SMBs | Timeline Impact |
|---|---|---|---|
| Level 1: Basic | 17 controls for safeguarding | Free NIST templates, quarterly self-audits | Immediate, low-cost entry |
| Level 2: Advanced | 110 practices, POA&M allowed | Outsource gap analysis, train via online certs | 6-9 months to certify |
| Level 3: Expert | 110+ enhanced, govt assessments | Collaborate on AI monitoring, phase hardware upgrades | 12+ months, grant-eligible |
| Level 4-5: Proactive | Metrics-driven, adaptive | Benchmark with peers, invest in blockchain tracing | Ongoing, for prime contractors |
By November, compliant firms report 20% faster bids, proving preparation pays dividends in a competitive field.
FAQ 18: What Emerging Challenges Are Arising in Space Cybersecurity This Year?
Space cybersecurity in 2025 is grappling with unprecedented challenges as low-Earth orbit swells with 10,000+ satellites, creating a vast attack surface. Jamming and spoofing lead the pack, with non-kinetic strikes during conflicts disrupting GPS for commercial launches—evident in 237 operations tied to the Gaza tensions. These invisible assaults mislead navigation, risking collisions in crowded orbits.
Supply-chain exploits compound risks, as seen in Iran-backed campaigns targeting virtual desktop providers for backdoor access to telemetry data. Quantum threats loom larger, with algorithms nearing maturity to decrypt legacy encryptions, prompting urgent migrations to post-quantum standards. Resource constraints hit smaller operators hardest, lacking AI for anomaly detection amid talent shortages.
Yet, innovations like digital twins simulate orbital hacks, refining defenses pre-launch. International pacts, via ICAO extensions, share intel on counterspace tactics from actors like China. These hurdles demand agility, but overcoming them secures the final frontier for all.
FAQ 19: Why Is Ransomware Surging in Aviation, and What Are Key Case Studies from 2025?
Ransomware’s surge in aviation stems from the sector’s data riches and operational dependencies, with a 600% jump in attacks by mid-2025 as groups eye quick payouts from disrupted hubs. Legacy systems and global supply chains provide easy footholds, turning a single encryption event into widespread paralysis.
Case in point: the March Kuala Lumpur Qilin hit, where 2TB of ops data was locked, forcing manual fallbacks and a rejected $10 million demand—costing $15 million in losses. September’s Collins Aerospace assault by Everest exposed mismanagement claims, delaying 500 flights across Europe without ransom, but sparking insurance probes. WestJet’s June social-engineered breach, tied to Scattered Spider, halted apps mid-season, underscoring human vectors.
Lessons? Backups and segmentation curtailed spreads, but the trend warns of escalation. Airlines counter with AI honeypots, luring attackers into traps.
- Qilin Tactics: Multi-stage encryption via unpatched servers.
- Everest Claims: Data dumps over demands, eroding vendor trust.
- Scattered Spider: Phishing blends with credential stuffing.
FAQ 20: What Does the Future Hold for International Cooperation in Aviation Cybersecurity?
International cooperation in aviation cybersecurity is poised for deeper integration by 2026, building on 2025’s momentum to counter borderless threats. ICAO’s strategy expansions emphasize real-time intel sharing, as seen in joint responses to UNC1549’s Middle East espionage, linking phishing to stolen aerospace IP.
Alliances like Five Eyes extend to orbital defenses, pooling data on jamming from Russia and China. IATA’s fact sheets guide harmonized regs, easing EASA-FAA alignments for drone traffic. Challenges like varying enforcement persist, but blockchain-secured platforms promise tamper-proof exchanges.
This collaborative fabric not only halves breach times but fosters inclusive growth, ensuring emerging markets aren’t sidelined. In a unified front, aviation’s digital guardians pave safer global routes.
| Alliance/Body | 2025 Focus | Future Projections | Benefits |
|---|---|---|---|
| ICAO | Threat sharing protocols | AI-integrated global dashboards by 2027 | 50% faster alerts |
| IATA | Best-practice compendiums | Annual cyber drills with 100+ carriers | Standardized responses |
| Five Eyes | APT attribution | Quantum-safe comms standards | Espionage deterrence |
| ENISA | EU space reports | Cross-continental exercises | Reduced orbital risks |

